UnCrackableL1-with-RMS
Tutorial: Solving UnCrackable Android App Level 1 with RMS
Solving UnCrackable Android App Level 1 with Runtime Mobile Security (RMS), based on this video
WARNING
This tutorial is under construction!
| Version | 2022.04.08 |
|---|---|
 |
This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License |
Table of Contents
Requirements
- NodeJS installed on your computer
-
[How To Install Node.js 14 on Ubuntu 22.04 20.04 18.04](https://computingforgeeks.com/install-node-js-14-on-ubuntu-debian-linux/) - How to Install Node.js and NPM on Windows
-
- FRIDA tools (client and server)
- as explained in the “Tutorial: Android Network Traffic Interception” and follow the Bypass Certificate Pinning section
NOTE
This tutorial might not work with an Android Virtual Device due to the limitations of the used tools. These instructions were tested on a Samsung A40 running Android 10.
Installation of Runtime Mobile Security (RMS)
- Open the terminal and run the following command to install the npm package:
> npm install -g rms-runtime-mobile-security
- Make sure
frida-serveris up and running on the target device and make a quick test:
> frida-ps -Uai
PID Name Identifier
---- ----------------------- ---------------------------------------
2164 Calendar com.google.android.calendar
1297 Google com.google.android.googlequicksearchbox
...
- Launch RMS via the following command:
> rms
RMS - Runtime Mobile Security
Version: 1.5.11
by @mobilesecurity_
Twitter Profile: https://twitter.com/mobilesecurity_
_________________________________________________________
Running on http://127.0.0.1:5000/ (Press CTRL+C to quit)
- Open your browser at
[http://127.0.0.1:5000/](http://127.0.0.1:5000/)and this is how it looks:

On Device detected you should see your Android Emulator.
NOTE
If RMS is not able to detect your device, please perform the following checks:
- check if
frida-serveris up and running on the target deviceRMSmust be started afterfrida-server- make sure that only 1 device is connected to your computer,
RMSis currently not able to detect multiple devices- kill
RMSand start it again
Solving UnCrackable Android App Level 1
There are two steps to solve this challenge:
- bypass the root detection protection
- discover the secret value inside the app
Bypass the root detection protection
First, download the UnCrackable-Level1.apk app, then install it:
> adb install UnCrackable-Level1.apk
Success
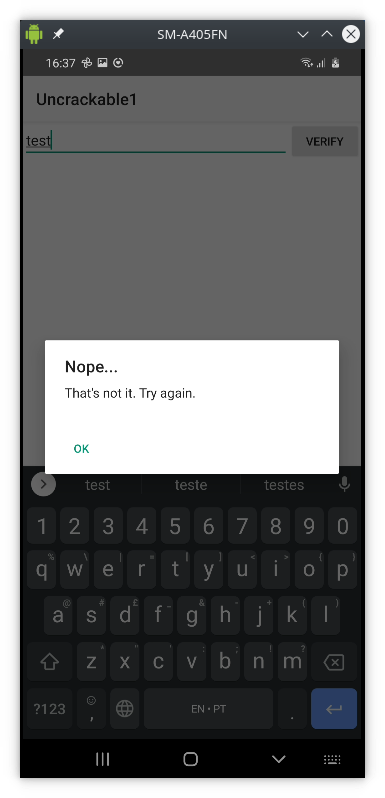
Now, run the Uncrackable1 app and you should see this error message:

The app is able to detect that it’s running on a rootedf device and exists. This is a common security mechanism used to prevent man-in-the-middle attacks. However, this is exactly want we want to do in order to study the app behaviour.
The next step is to trick the app to believe the device isn’t rooted. This can be acheived with a frida script, but RMS already has some built-in scripts for thid purpose. The next steps are:
- under
Mobile OSchooseAndroid - under
Package nametypeowasp.mstg.uncrackable1frida-ps -Uaiwill list all installed apps and their names
- click
Load Default Frida Scriptsand choose[24] system_exit_bypass.js(the number might be different depending on the installed version) - click the button
Start RMS - now go to the Android device, the app
Uncrackable1should be open and show the sameRoot detectederror- what happens now if you click
OK? - the app should stay open inspite of the error message
- what happens now if you click
- type
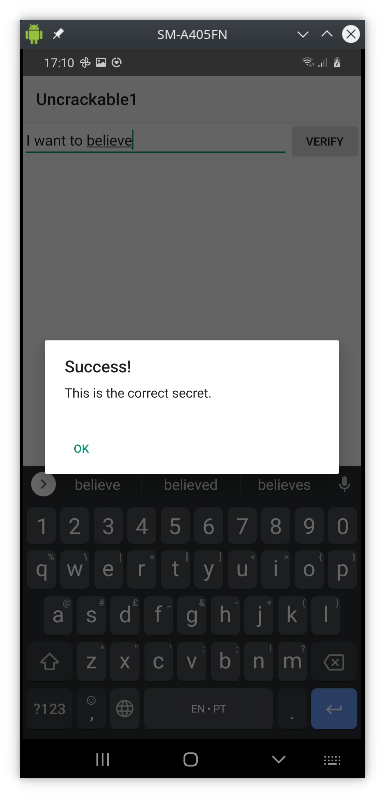
testin theEnter the Secret Stringfield and clickVERIFY
Discover the secret value inside the app
On the RMS tool:
- click the botton
Load Classes - click the botton
Insert a Filter - insert in
Hook all classes that start withfield the textsg.vantagepoint - then click
Submit - here’s what you should have by now:
- then click the button
3. Load Methods - followed by the
4. Hook all methodsbutton
On the Android device:
- hit the
VERIFYbutton again
Here’s what you should have now on RMS

Still on RMS:
- go to the
Dump TABand check that thepublic void verify()is listed - (explain the source code)
- go to the
Load Frida Scripttab - on the left pane, click on
[25] - tracer_cipher.js(the number might be different depending on the installedRMSversion) - click in the
Run Custom Frida Script
On the Android device:
- hit the
VERIFYbutton again
On RMS tool:
- scroll the results inside the
Global Console Output - here’s the result: